Most well-publicized events have accompanying spam runs, like the death of a famous person or large sporting events. Most of you will have seen a news-related e-mail at some point that turned out to be just another spam message trying to sell you a replica watch.
However, some events, though very well-publicized, don’t generate the same kind of rush in the spammers’ world probably because they believe their target audience would not be very interested in the topic, and so would be less likely to fall for any related scams.
Examples of this type of event are the semi-annual G20 summit and the annual G8 summit. These events seem to be of little interest to general spammers. We have not seen any of the usual types of spam referencing it in any way. But even though they are not exploited in the same way as an event like the World Cup, they still do not escape the notice of cyber criminals.
A large political event like the G20 or G8 summit is a key opportunity for cyber criminals who want to try and gain access to political systems, and therefore at times leading up to, or around, an event like this we see an increase in the number of targeted attacks. A targeted attack is a specially crafted e-mail sent to a specific individual, or small group of individuals, in order to try and gain access to specific systems.
At times when large political events are happening, it is more likely for people working in public office, or other public services, to receive unsolicited e-mail on the topic of the event. This can present an opportunity for a criminal to bypass security with some social engineering.
Targeted attacks usually differ from standard spam as the perpetrators spend more time making them look genuine. For example, see the screenshot of a targeted attack e-mail below. This is a well-written, relevant e-mail all designed to make it seem as legitimate as possible, in the hopes that this will convince the victim to open the attached file, which in this case is a malicious pdf.
Some of the targeted attacks are more like standard spam. The scammers don’t bother with the long accompanying text. They just send a blank e-mail with an attachment, or sometimes a single line saying “see attachment” or similar. What is different from normal spam, though, is that the subject line and attachment name are designed to be relevant to the person being targeted, so they are more likely to open it to see what is inside, allowing their machine to get infected at the same time.
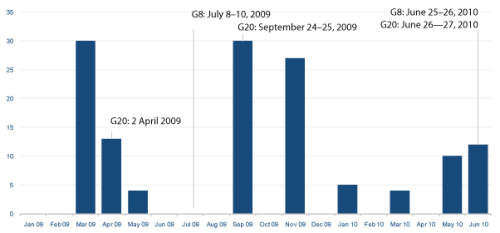
When the G20 summit happened in April 2009, MessageLabs Intelligence saw a record number of targeted attacks in March in the last couple of weeks leading up to the summit. We saw another surge in targeted attacks between the G8 summit in July 2009 and the G20 summit in September 2009. With the next G8 and G20 summits in Canada this weekend, we are yet again seeing the number of targeted attacks on this topic increase, and we expect to see this trend continue until at least next week when the summits have finished.
All the targeted attacks we have seen relating to the G8 and G20 summits have been attempts to infect a national or local government using exploits in the well-known file formats .doc and .pdf, which are widely used in business environments.
As the summits go on, we expect to see the attempted targeted attacks continue. While those in public office may not be able to ignore all unsolicited e-mail, you can still protect yourself. Think carefully before opening an attachment.
You could try looking up the person to see if they are genuinely who they say they are. If a mail with an attachment comes from webmail it is less likely to be a reputable source. Most importantly though, keep all your anti-virus software up to date, and make sure you have all the latest application patches installed as these updates fix software vulnerabilities as they are found.
Mathew Nisbet is a Malware Data Analyst for Symantec Hosted Services