It’s dubbed the Golden Cash network, and serves as a type of online exchange for cybercrooks to buy and sell access to batches of compromised PCs.
The reach and impact of Golden Cash botnet (a network of commandeered PCs) is far more extensive than the “average affiliation network operated by cyber criminals,” according to security firm Finjan Inc.
It was Finjan that first exposed the operations of this unusual and powerful botnet. Finjan’s recently published Cybercrime Intelligence Report of 2009 (second issue) details the sinister – and highly organized — operations of the Golden Cash Network.
Read related stories
Brutal botnet steals data from 180,000 hacked computers
Relentlessly stalk and shatter hacker groups, expert urges
After brief respite beastly botnets are “back with a vengeance”
Hacker compromised legit Web sites now pose gravest danger
“Our research showed there is something really major behind this one — an entire trading platform of malware-infected PCs,” the Finjan report notes.
Besides serving as a user-friendly “trading platform” for malware infested PCs, Golden Cash offers “buyers and sellers” all the tools they need to carry out their nefarious trade. For instance, “it provides an exploit toolkit with obfuscated code and an attack toolkit to distribute malware.”
Modus operandi
Golden Cash exemplifies a fast growing trend in the cyber underworld — online trading (buying and selling) of access to compromised PCs on a botnet.
Cybercriminals pay for this access so they can install malware on the PCs and then use these machines for criminal activities such as stealing data or sending spam.
For cybercrooks, buying or selling access to compromised PCs on a botnet may often be far more lucrative than peddling stolen data, such as credit card numbers, SSNs or confidential e-mail communications.
And sales of compromised PCs are highly structured.
Golden Cash Home Page
“It doesn’t matter if it is a home computer or belongs to a C-level executive [at] a Fortune 500 company, government agency or news network,” said the Finjan report. “Each compromised PC has its own value and price.”
And territorial and geographic factors determine the price tag of captured PCs – which are sold in batches of 1,000 on the Golden Cash portal.
For instance, a “price table” included in the Finjan report, reveals huge price variations for access to hacked computers, based on country.
Prices range from $100 for access to 1,000 infected machines in Australia to only $5 for a similar batch in other countries, mainly in the Far East.
Buyers and sellers
Buyers can also mix-and-match infected PCs purchased, selecting them from a range of territories, instead of a single country.
As the Finjan report notes, the cybercrooks “know that they can sell these assets online anytime they want later on – the market is there to stay.”
The Golden Cash site offers several payment options, including WebMoney and Western Union money transfer.
Much like in any market, “traders” in compromised PCs make money by buying low and selling high.
The Golden Cash price list – included in the Finjan report – indicates that the going rate for control over a batch of 1,000 malware-infected PCs from Australia is $500.
Their purchase price is only $100, which translates into a profit of $400 per batch, the Finjan report notes.
Partners in crime
Traditionally in the botnet business, “partners” are often recruited by botmasters or hackers.
These partners embed malicious code on their own Web sites, designed to infect and compromise the PCs of visitors to their site and are paid for each infected computer.
Golden Cash online network uses a variation of this modus operandi.
The partner is recruited and paid specifically to distribute the Golden Cash bot on legit Web sites – and are provided with tools to execute this task.
Finjan researchers were able to study the methodology used to expand the Golden Cash botnet by monitoring the operations of a Golden Cash “partner” — a cybercrook codenamed “Razor.”
The step-by-step process is detailed on the Finjan blog.
Here’s how it works:
A user visits a legitimate compromised Web site that contains a malicious iFrame. The iFrame causes the victim’s browser to pull the exploit code from a server armed with the exploit toolkit.
Upon successful exploitation, a special version of a Trojan, especially created for the attacker, is pulled from the Golden Cash server and installed on the victim’s machine.
From there, it reports back to its “master” — the Golden Cash server.
The victim’s machine is now in a pool of infected machines controlled by Golden Cash, and the attacker’s account at Golden Cash is credited with payment for the job done.
The first instruction sent by Golden Cash to the victim’s machine, is to install an FTP grabber to steal FTP credentials.
Finjan researchers were able to identify around 100,000 domains whose FTP credentials were stolen, enabling the partners to access these servers. Corporate domains across the world featured on this list.
The researchers also tracked the buy/sell operations on the Golden Cash trading system as they happened.
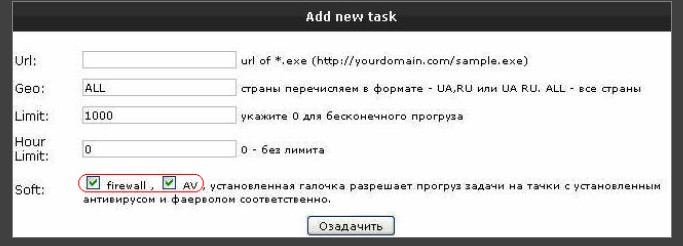
For instance, they captured the transaction of a “client” with two outstanding orders: one for 3,000 infected PCs and the other for 1,200.
A customer can also add additional criteria when selecting which PCs to access – this may be a preferred geographical area or machine that’s not protected with firewalls and anti-virus software. (See screenshot below).
While their methodologies may differ, nearly all botnet-related abuse today is driven by financial considerations.
And the modus operandi used by bot herders and others in the “bot ecosystem” is also very similar.
It’s outlined by Jim Lippard, a Pheonix, Az.-based technology consultant, who has written and spoken widely on the botnet menace:
- Viruses and worms are used to compromise systems to use as bots.
- Bots are used to send spam to sell products and services (often fraudulent), engage in extortion (denial of service against online gambling, credit card processors, etc.), send phishing emails to steal bank account access
- Access to bots as proxies (“peas”) is sold to spammers, often with a very commercial-looking front end Web interface.
Lippard was formerly director of information security operations at network services provider Global Crossing, whose customers include more than 35 percent of the Fortune 500, as well as 700 carriers, mobile operators and ISPs.
Beating botnets
What can be done to combat the menace?
Most leading anti-virus products have botnet removal capabilities.
However, Finjan’s Cybercrime Intelligence Report cites the limitations of AV software.
While they do a “good job in cleaning infected machines”, it says AV applications are essentially reactive, and aren’t designed to prevent a PC from being compromised and turned in to a bot.
For this, Finjan says, a pro-active approach is needed.
“The preferred line of defense is a secure Web gateway, utilizing active real-time content inspection. By understanding the intention of the code, such a Web security solution detects and blocks malware regardless of its source, even when the code is obfuscated.”
Lippard recommends a holistic approach to battling bots — one that includes participation of a broad range of stakeholders, from network service providers (NSPs) and ISPs to law enforcement personnel to end users.
He has the following suggestions for NSPs and ISPs
- Screen prospective customers against ROKSO and other publicly available information sources. (ROKSO is a register of known hard-line professional spam operations that have been thrown off ISP services three times or more)
- Strengthen acceptable use policies and contracts to allow rapid removal of miscreants
- Secure company end-user machines with endpoint security
- Monitor for malicious traffic (or interact with security researchers or upstreams who monitor); notify downstreams and escalate if they fail to act.
- Filter and terminate abusers.
- Nullroute bot controllers and phishing Web sites
- Collect actionable intelligence and notify law enforcement




