Google Inc. is warning Gmail users to activate two-step verification to protect their accounts after the discovery of what is being called a highly effective phishing technique targeting Gmail and other services that tricks recipients into giving away their login credentials.
The technique, which spoofs a Google address, has been used for several months but got attention last week with the publication of an alert from WordFence, which makes a WordPress security plug-in. Briefly, an attacker sends an email to the target’s Gmail account which comes from someone the recipient knows but who’s account has been hacked. The email includes what appears to be an image of an attachment.
When the target clicks on the image a new tab opens up the recipient is seemingly prompted by Gmail to sign in again. If the target looks at the URL bar they might see something that includes accounts.google.com to make the message look legitimate — like this:
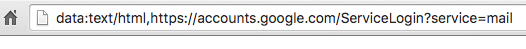
(Image from WordFence)
Having captured the target’s login, a process is started where malware grabs names in the contact list and emails the message to them — and the attacker has access to all of the recipients’ mail.
In a statement Tuesday a Google official said: “We’re aware of this issue and continue to strengthen our defenses against it. We help protect users from phishing attacks in a variety of ways, including: machine learning based detection of phishing messages, Safe Browsing warnings that notify users of dangerous links in emails and browsers, preventing suspicious account sign-ins, and more.”
This technique isn’t only being used for Gmail, and can be used on any messaging platform. One of the first warning signs is an application that asks a user to sign in a second time.
WordFence warns people that a better warning is right in front of the user: Instead of the URL starting “https…” it starts “data:text….”
CISOs should warn employees that when signing into ANY service check the browser location bar and verify the protocol, then verify the hostname. It should look like this in Chrome when signing into Gmail or Google:
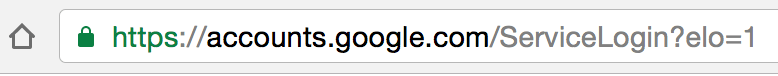
Enabling two-factor authentication in any messaging app will also help if the user has made a mistake.
That green coloured “https” is another sign things are all right. This is what a URL bar looks like if things are bad:
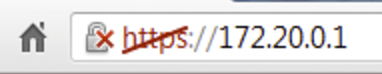
WordFence also notes that if you use Gmail, you can check your login activity to find out of someone else is signing into your account by going to https://support.google.com/mail/answer/45938?hl=en. Scroll to the bottom of your inbox and click “Details” (very small in the far lower right hand corner of the screen). This will show all currently active sessions as well as recent login history. If there are active logins from unknown sources, you can force close them. If you see any logins in your history from places you don’t know, you may have been hacked.





