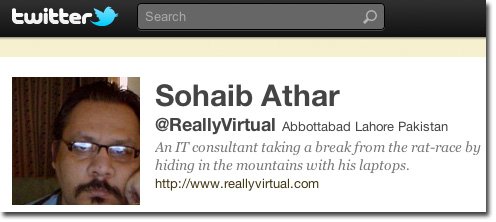
On Sunday, a Twitter account called @ReallyVirtual based in Abbottaba, Pakistan, tweeted about helicopters and explosions in the area, just about six hours before news broke that United States intelligence operatives have attacked the hideout of fugitive Al Queda leader Osama bin Laden. It would appear that tweeter, Sahaib Athar, was present during the attack. Naturally this generated lots of interest in the microblogging site and soon Athar’s tweets become a major source of media interest and the public seeking more information on the news.
Unfortunately, people who followed the link Sahaib Athar’s blogsite found their computers compromised. Online security firm Websense told ITBusiness.ca yesterday that its Security Labs discovered that the Web site belonging to Athar been compromised by hackers and leads to the Blackhole exploit kit. “The site was actually serving a poorly detected malware,” according to Patrik Runald, senior manager for Websense’s Security Labs.
He also described the Blackhole Exploit Kit as a do-it-yourself, drive-by exploit that keeps trying multiple vulnerabilities to compromise an end user’s computer. “The kit allows individuals with little or no coding knowledge to deliver many different types of malware, from scareware or Rogue AV to custom Trojans that steal information or online banking credentials.” The kit, Runald said, was recently used to exploit websites belonging to the USPS, for example.
Related stories
Malware, spam in 10 per cent of Facebook links
Social networks teeming with spam and malware
In Athar’s case, cyber criminals had infected his blogsite to serve up fake system scanners. Users who visit the site get a spoofed warning that their machines or Internet connection has been compromised. “To get rid of the malware, victims are asked to pork out $79.95 to purchase a anti-malware tool. Of course that tool is actually useless,” said Runald.
Runald also told ITBusiness.ca that legitimate media sites might actually have been “delivering” computer users to the infected Web site of Athar according to the Websense security expert. “What is amazing in this circumstance is that we saw stories from huge newswires and big online publications like CNN/Money link to this Twitter account which then had the link to the infected Web site.”
Runald said that before the killing of bin Laden, Athar had only 15,000 Twitter followers. But after sites such as CNN began retweeting his post, that number ballooned to 71,000 by early Monday morning.Clicking on his Twitter accountis safe, it is Athar’s blogsite that contained the malware.
Athar’s site has since been “cleaned” but the blogger is still using an older version of WordPress that is still vulnerable to attacks, according to Runald.
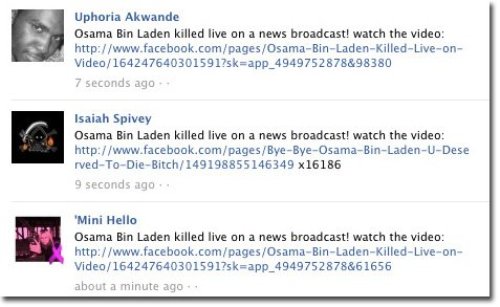
Early Monday morning, the security company also found that spam exploits have made their way to Facebook. Websense’s Security Labs Blog said posts purporting to contain links to a video of a slain bin Laden have been popping up in the popular social networking site.
“When clicking on the link the user is taken to a page on Facebook asking them to copy/paste the code into the browser’s address bar so that they can watch the video,” said the blog. But the link does not lead to a video at all, according to the report. By clicking on the link “all you do is to help spread the message so don’t do this,” according to the blog.
Websense has discovered at least three variants of Facebook scams related to bin Laden’s death. “The one we reported on our blogsite purports to have a link to a video of the raid,” said Runald. “ Victims are asked to fill out a survey to get to the video but in reality there is no video. When people answer the survey they simply help the scammers earn money.”
Despite repeated warning, many people continue to spread the link among the Facebook friends, said Runald.
While any Al Queda counter attack that espionage and military experts have been talking about has yet to materialize, malware creators are already using the news of Bin Laden’s death as a opportunity to try and dupe people into clicking on malicious links. According to cloud-security firm Zscaler, researchers were already seeing malicious sites emerge to capitalize on the news within hours of the announcement.
Zscaler uses the example of one Spanish language site that displays a purported photo of a murdered Osama bin Laden and includes a story about the US led operation. The page includes a Flash Player window with a message indicating that the user must first update a VLC plugin, which is a popular media player, in order to view the video. The link is, unsurprisingly, a bad one, said researchers.
“When the user clicks on the link, they will download a file titled XvidSetup.exe. This file is actually a popular adware tool known as hotbar,” according to the Zscaler blog post, which also notes 19 of 41 antivirus engines are blocking the file at this time.
According to a post from Randy Abrams, Director of Technical Education, Cyber Threat Analysis Centre, ESET North America, black hat SEO manipulators know all too well that big headlines mean people will search for news, and they also know how to make their malicious sites show up early in the search results. Cyber criminals also use a slew of social engineering and phishing techniques to lure people into malware traps.
“Always stick with well known sites for your news information,” advises Abrams. “You can go to sites you haven’t heard of before, as long as they are coming recommended by friends and you know that your friend actually did recommend them. That means a simple email, IM or Facebook post doesn’t cut it& you don’t know if your friend’s account was compromised. You need to have a dialog with your friend.”
Experts also advise being wary of shortened links on Facebook and Twitter that claim to lead to Bin Laden news. Obscured links are a popular way to con computer users into clicking on a malicious link.
Security firm Sophos warned Monday to watch out for links in email or on social networking sites offering additional coverage of the event.
“Many of the links you see will be perfectly legitimate links,” said Sophos’ Paul Ducklin in a Naked Security blog post. “But at least some are almost certain to be dodgy links, deliberately distributed to trick you into hostile internet territory.”
Ducklin offers several tips to avoid being trapped. They include:
1)Don’t blindly trust links you see online, whether in emails, on social networking sites, or from searches. If the URL and the subject matter don’t tie up in some obvious way, give it a miss
2)Use an endpoint security product which offers some sort of web filtering so you get early warning of poisoned content.
3)If you go to a site expecting to see information on a specific topic but get redirected somewhere unexpected – to a “click here for a free security scan” page, for instance, or to a survey site, or to a “download this codec program to view the video” dialog – then get out of there at once. Don’t click further. You’re being scammed
Researchers with Imperva captured the inner workings of a black-hat SEO effort on a hacker forum. In Imperva’s blog post, they provide details on the campaign, which is designed to generate inauthentic Facebook likes through obfuscated links.




