In the beginning was the firewall, and it was pretty good. A big box of rules that sat between your network and the evils of the Internet, the firewall examined ports and protocols to decide which packets got in and which were barred at the door.
Then things got, as things often do, complicated. New threats came sneaking in on trusted protocols, ports and protocols became tangled, and looking inside packets became just as important as noting their source, destination, and type.
Protecting a network now meant deploying multiple firewall types (network, endpoint, application), anti-virus protection, content filters, intrusion detection systems, and more. Instead of a big box of rules, you needed a relay rack stuffed top to bottom with appliances – each with its own administrative interface, and each representing a possible point of failure in the network.
There had to be a better way, especially for smaller companies that couldn’t afford a massive staff to feed and care for the relay racks full of appliances — and thus, the unified threat manager (UTM) was born.
Indeed, a rapidly growing number of small and mid-size companies are opting for the administrative and operational simplicity of the single-box solution. And so we decided that UTMs aimed at the mid-size company were the perfect group to use for the rollout of InfoWorld’s new firewall and UTM test protocols.
When we began this process well over a year ago, we asked for input from virtually every firewall and UTM vendor we knew, and we invited every UTM vendor we could find to send us an appliance to test. In the end, four vendors answered the call. Astaro, SonicWall, WatchGuard, and ZyXel submitted units for this first set of tests.
Although all four fulfill the basic definition of a UTM – combining firewall, VPN, intrusion detection and prevention, anti-malware, anti-spam, and Web content filtering – we could not have asked for four more diverse units.
There are differences in basic approaches to security (by default, allow most normal traffic or allow absolutely nothing), differences in administration capabilities, big differences in throughput, and most important of all, immense differences in effectiveness against malware.
UTMs unmasked
Among the four devices we tested, only one – the SonicWall NSA E7500 – provided a significant level of protection against malware, blocking 96 percent of the attacks we threw at it.
The Astaro Security Gateway 425 and WatchGuard Firebox Peak X5500 fell far short, blocking a mere 26 percent and 33 percent of the attacks, respectively. The ZyXel ZyWall USG1000 took the middle ground, blocking a more respectable 69 percent of the attacks. (See chart below.)
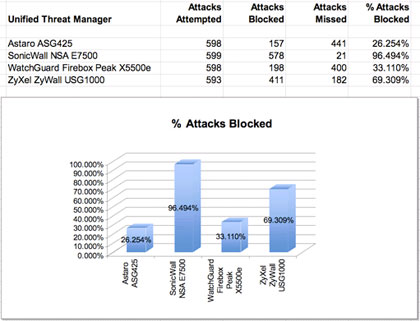
In InfoWorld tests, the SonicWall NSA E7500 blocked 96 percent of malware attacks.
It’s important to note that the attacks used in the test (Mu Dynamics’ Published Vulnerability Attacks, drawn from the US-CERT database) were all exploits of known vulnerabilities (no “zero day” surprises) in a wide range of popular operating systems, applications, and protocols (Microsoft Windows, Internet Explorer, Cisco IOS, Apache, SQL, ICMP, SSH, and so on).
We threw the full range of exploits at our UTMs, about 600 attacks in all, but the UTMs should have been designed to thwart such threats. And still hundreds were allowed to pass through.
Why did the UTMs miss so many exploits? We don’t know, but we suspect that (apart from the SonicWall) they lack the horsepower to perform the necessary deep packet inspection while under load. At the same time the UTMs handled our attacks, we were pushing the limits of their throughput with legitimate traffic. The upshot is, although the vendors have packed these devices with additional gateway security functions, clearly many UTMs are still strictly firewalls at heart.
UTM functions require gobs of processing in order to peek into packets to look for malware, so it should be no surprise that the devices — all except the Astaro — took a significant hit in throughput when under attack. Compared to their maximum throughput without attacks, the WatchGuard took a 45 percent hit, the ZyXel 36 percent, and the SonicWall 23 percent.
The Astaro, which blocked the fewest attacks in our test, barely lost a step when under attack — a surprisingly tiny 2 percent dip from maximum throughput. Generally, however, you should be prepared for huge hits to throughput when you turn on all of the security functions of a UTM. You are not getting a wire speed device. On the plus side, unless your WAN link is a gigabit Ethernet feed, you may never notice the slowdown.
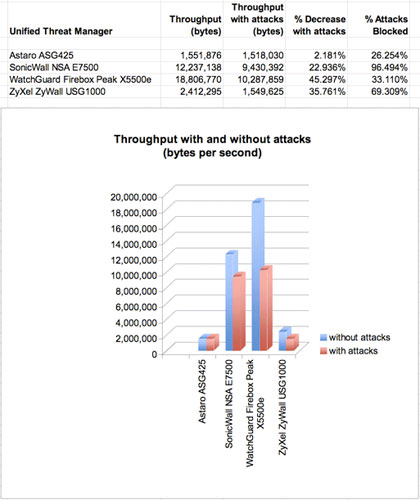
All the devices except the Astaro took a significant hit in throughput when under attack.
Recognizing a winner
Despite the poor attack blocking test results, each of these “UTMs” will serve as perfectly effective firewalls and VPN appliances, if they’re installed and administered properly. There were no crushing disappointments here and no products that we have to warn companies not to consider. Instead, there were four variations on firewall competence, with enough brilliance thrown in to make life good for the security folks at quite a few mid-sized enterprises.
So who won? We do have a clear overall victor in the group, but before we get to that, let’s talk about the winners in several important categories. If initial purchase price is your primary consideration, then ZyXel has a UTM for you. Make sure to keep tabs on just how much bandwidth you ask the ZyXel to protect, because it runs out of steam much earlier than the SonicWall and WatchGuard appliances.
But at one-fifth the cost of the Astaro, the ZyXel ZyWall ($3,399 as tested) provides just as much throughput and twice the attack protection. Playing within its limits, the ZyWall is a solid, economical choice for organizations with smaller, less-demanding networks.
Maybe your primary criteria is out-of-the-box safety, though your system will require substantial customization before your users are all happy. It sounds like the WatchGuard system is for you. Also a terrific value (at $9,299 as tested), the WatchGuard Firebox lays claim to enterprise-class manageability and the most throughput in our test. This is a firewall with plenty of headroom.
If you seek the greatest number of functions in a single box, the Astaro Security Gateway appliance brings an incredible range of security options to the table in a Linux-fueled package. The Astaro is even available as a VMware virtual machine, if protecting your company’s virtual server farm is what you have in mind. However, the Astaro pulls up short on attack protection and throughput, especially for the price ($18,565 as tested).
Finally, if you need nothing short of the most serious combination of uncompromising security and maximum throughput, the SonicWall NSA is your box. The clear winner of our test, the SonicWall ran only a step behind the WatchGuard in throughput and far surpassed all three competitors in attack protection. Add its wizard-based setup routine that steps administrators through an otherwise complex process, and you have a product that clearly benefits from being the sixth generation of its family.
The purchase price of the SonicWall NSA E7500 ($38,990 as tested) is significantly higher than the other appliances here. But its combination of attack defense and throughput arguably shows an even greater gap from the competition. The SonicWall is not only a UTM truly worthy of the label, but a mid-range UTM that could well keep company with much larger devices.
Brian Chee is a senior contributing editor to the InfoWorld Test Center and the founder and manager of the Advanced Network Computing Laboratory at the University of Hawai’i School of Ocean and Earth Science and Technology.
Curtis Franklin Jr. is a senior contributing editor to the InfoWorld Test Center.
Source: Infoworld.com




