Every company in every conceivable industry is compromised by hackers – or will be shortly – according to a report from McAfee, a major maker of cybersecurity software.
“I am convinced that every company in every conceivable industry with significant size and valuable intellectual property and trade secrets has been compromised (or will be shortly), with the great majority of the victims rarely discovering the intrusion or its impact,” Dmitri Alperovitch, McAfee’s vice president of threat research, wrote in the report, “Revealed: Operation Shady RAT.”
“In fact,” he added, “I divide the entire set of Fortune Global 2000 firms into two categories: those that know they’ve been compromised and those that don’t yet know.”
In the report, McAfee revealed that more than 70 organizations around the world –including the United Nations, several national Olympic committees, 13 defense contractors and governments in the United States, South Korea, Taiwan, Vietnam and India — had been compromised in an operation the company is calling “Shady RAT.”
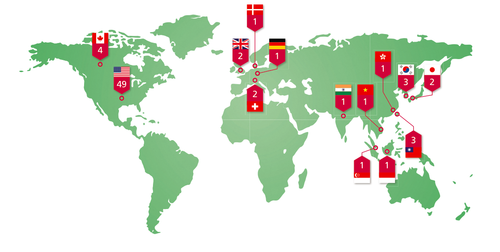
McAfee reports four Canadian targets were hit: two government agencies, an IT firm, and the World Anti-Doping Agency.
According to McAfee, its analysis of Shady RAT is “the most comprehensive analysis ever revealed of victim profiles from a five-year targeted operation by one specific actor.”
“After painstaking analysis of the logs, even we were surprised by the enormous diversity of the victim organizations and were taken aback by the audacity of the perpetrators,” wrote Alperovitch.
“This is not a new attack, and the vast majority of the victims have long since remediated these specific infections (although whether most realized the seriousness of the intrusion or simply cleaned up the infected machine without further analysis into the data loss is an open question),” the report added.
The Shady RAT data thefts are just a small part of a larger picture, the report noted. “What is happening to all this data … is still largely an open question,” it acknowledged.
McAfee gathered the information for its report by cracking into a command and control server used by the hackers and accessing logs on the machine that detailed the bandits’ activity.
In its report, the company contended that Shady RAT had the fingerprints of a nation state on it. The “interest in the information held at the Asian and Western national Olympic Committees, as well as the International Olympic Committee (IOC) and the World Anti-Doping Agency in the lead-up and immediate follow-up to the 2008 Olympics was particularly intriguing and potentially pointed a finger at a state actor behind the intrusions, because there is likely no commercial benefit to be earned from such hacks,” McAfee reported.
McAfee did not say what country might have been working with the hackers, in contrast to companies such as Google, which as recently as last month blamed China for hacking into the Gmail accounts of several high-profile U.S. officials.
The report noted that the shortest time an organization was compromised was less than a month, a distinction held by nine of the targeted entities. But Alperovitch cautioned that “that this may not necessarily be an indication of the rapid reaction of information security teams in those organizations, but perhaps merely evidence that the actor was interested only in a quick smash and grab operation.”
Alperovitch wrote that over the past five to six years there has been nothing short of a “historically unprecedented transfer of wealth” due to the hacking operation.
The data stolen consists of everything from classified information on government networks, source code, e-mail archives, exploration details for new oil and gas field auctions, legal contracts, SCADA (supervisory control and data acquisition) configurations, design schematics and more, Alperovitch said.
McAfee declined to name most of the organizations attacked, referring to businesses such as “South Korean Steel Company,” “U.S. Defense Contractor #1” and “Taiwanese Electronics Company,” among others.
In 2006, eight organizations were attacked, but by 2007 the number jumped to 29 organizations, according to the report. The number of victimized organizations increased to 36 in 2008 and peaked at 38 in 2009 before starting to fall, “likely due to the widespread availability of the countermeasures for the specific intrusion indicators used by this specific actor,” Alperovitch wrote.




