Canadian companies and consumers are among those affected by a gargantuan global hacker attack that’s infected 1.9 million computers worldwide with malware, according to security firm Finjan Inc.
This colossal botnet (network of hijacked computers) is “one of the largest controlled by a single team of cybercriminals” found this year, Finjan researchers say.
It was discovered by Finjan’s Malicious Code Research Centre (MCRC), and the announcement made on Wednesday at the RSA Conference 2009, a high-profile information security event being held at Moscone Centre in San Francisco.
Headquartered in San Jose, Calif., Finjan Inc. is a provider of Web gateway security products
The botnet was created by a group of six persons with a server located in the Ukraine that’s been used to perpetrate such attacks since February 2009.
“As folders on this server were left open, we were able to get more information for our research,” Finjan researchers said in blog posting.
While around 1.9 million computers were infected at the time of the posting, the researchers say they have seen this number “increase on an hourly basis.”
Snapshot of number of infected computers
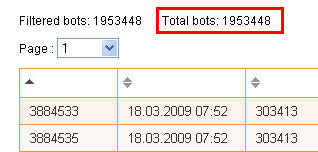
This discovery was made in the course of an investigation the Research Centre was conducting of command-and-control servers operated by cyber-criminals.
Affected countries
“What makes this so different is that the rate of infection is so high,” the company said in a statement. “Corporate, government and consumer computers around the world have been infected by the malware.”
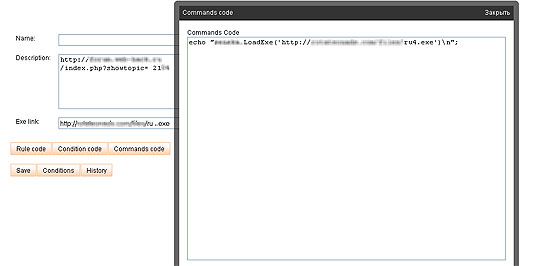
Example of a command sent to infected machines
Forty-five per cent of the 1.9 million infected computers are from the U.S. – which tops the list of affected countries by a very wide margin.
Other countries most affected by the bot blitz are: the U.K. (6 per cent of the machines), Canada (4 per cent), Germany (4 per cent) and France (3 per cent).
An assortment of other countries account for the remaining 38 per cent of compromised computers.
According to Finjan, these cybercriminals have established a vast affiliation network across the Web to successfully distribute and operate their malware install base.
Compromised machines have been detected in at least 77 government-owned domains (.gov) in various other countries.
Command and control
The command-and-control server used by the cybercrooks has a powerful backend management application, Finjan researchers say, making it easy for the attackers to manage the infected machines.
“One of the management console features we identified is a Command Editing panel through which instructions are sent to the infected machines (bots). We have seen commands asking the bots to download and execute additional malware, download settings files, apply update files etc.”
Infected machines are instructed to download and execute a Trojan horse, and that, in turn, later installs a group of other malicious executables without the user’s consent.
“Downloaded files that were identified include SENEKA[removed].DLL; Zch[Removed].exe and many others,” said the blog post from the MCRC team.
When inspecting these files, Finjan researchers found they could perform the following actions:
- Read e-mail address and other details from the infected PCs;
- Communicate with other computers using HTTP protocol;
- Execute a process;
- Inject code into other processes;
- Visit Web sites without end-users’ consent;
- Register as a background service on the infected computer and a few dozen other commands.
Cybercriminals, the Finjan team says, can execute almost any command on the end-user computer as they see fit, including: reading e-mails, copying files, recording keystrokes, sending spam and making screenshots.
Virus Report (only four of the 39 anti-virus products detect the Trojan)
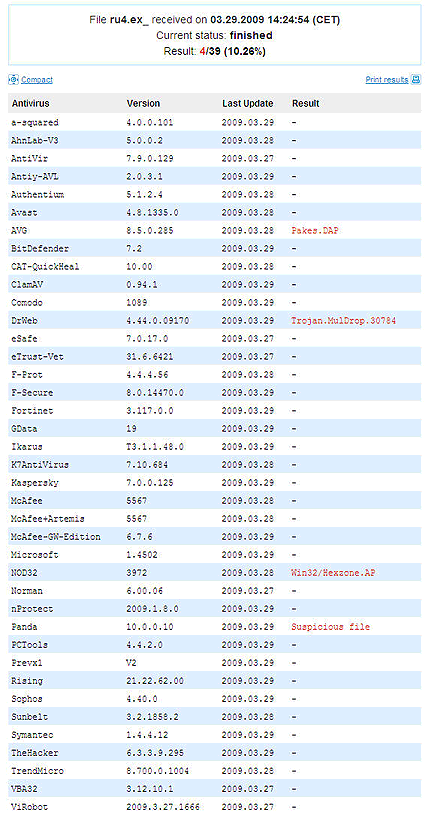
The security firm has apprised law enforcement authorities in the U.S. and the U.K. of its findings and provided them with information about the server. “Finjan has also contacted affected corporate and government agencies to let them know that they were part of the infected computer names.”
The sophistication of the malware and the “staggering” number of infected computers suggest that “cybergangs are raising the bar,” according to Finjan chief technology officer Yuval Ben-Itzhak.
Hackers, he said, are constantly on the look out for better methods to distribute malware “and Trojans are winning the race.”
Modus operandi
Malware is installed on computers when users visit compromised Web sites that serve malicious code, Finjan research reveals.
Information found on the command and control server includes the IP addresses of the infected computers, as well as the computers’ name inside corporate and government networks running the malware.
The infected computers were running Windows XP as the operating system, and the vast majority are using Internet Explorer ((78 per cent) as the Web browser.
In an e-mail to ITBusiness.ca, Ben-Itzhak confirmed that the bot isn’t related to the notorious Conficker (or Downadup) worm that also targeted Microsoft Windows operating systems.
He said given their popularity made Windows XP and Internet Explorer natural targets for this attack.
Other browsers being used on infected machines include Firefox –15 per cent, Opera – 3 per cent, and Safari – 1 per cent. Other browsers account for the remaining 3 per cent.
“An ounce of prevention”
What tools do companies and consumers have to protect their computers and prevent them from being commandeered, and becoming part of a bot net.
Finjan itself recommends an integrated Web security product, such as its own Unified Secure Web Gateway offering provides multiple layers of Web security,using real-time content inspection technologies, with data leakage prevention tools.
A Canadian analyst, however has a different take on the issue.
Most malware exploits known vulnerabilities, noted James Quin, senior research analyst at Info-Tech Research in London, Ont.
“For pretty much every known vulnerability, a patch is available,” he said.
And while, occasionally, a vulnerability is publicised before a patch is available, “the norm is that patches exist before vulnerabilities are made public.”
So Quin recommends a thorough patching program that eliminates the vulnerabilities even before they can be exploited. “I’m an ounce of prevention type of guy.”
But he also recognizes the need for a well-maintained anti-malware infrastructure (with coverage at least at the gateway as well as at the endpoint).
This, he said, is essential – “as is a firewall with carefully written and maintained rule set “that can block bots from communicating with a command-and-control server.
Finjan’s and its competitors’ products, Quin said, would have a role as a third or fourth (depending on how you want to break up the above list) layer of defence that analyzes Web traffic.
While by itself, such defence layer isn’t’ enough, he said, “it certainly helps to control the Web pipe which firewalls and anti-malware solutions can have problems with.”




