While Canadians today the option of using SMS and other social networking tools to deliver financial aid to tens of thousands of victims in the Haiti’s worst earthquake ever, cybercrooks have lost no time in using the same technologies to defraud would-be Good Samaritans.
Anti-virus software vendor, Cupertino, Calif.-based Symantec Corp. yesterday reported that 419-style online messages have began surfacing on the Web just two days after the catastrophe.
“The old, ugly 419 scam has reared its head once more,” Dylan Morss, senior manager, anti-spam systems at Symantec told ITBusiness.ca yesterday.
There’s no revolutionary twist, or novel technology involved here. The formula is similar to millions of 419-type messages in recent years, according to Morss.
Rather than pretending to be a person seeking to transfer huge sums of money to another account, this time around the spam sender purports to be a person of influence within a charitable group.
“The messages we’ve seen come from a sender claiming to be an officer of a group involved in relief efforts in Port-Au Prince, such as the Red Cross,” said Morss.
The message asks the potential donor to send funds “immediately” to a certain location via Western Union money transfer and to provide the sender with their name and address, exact amount sent, and money transfer transaction number.
Related stories:
Scammers & fraudsters extend Holiday earnings at Haiti’s expense
Hacked e-mail accounts used in 419 scam “with a twist”
Text messages that count – mobile giving for Haiti
Five formidable Facebook frauds and how to protect yourself
The decade of convergence and the (n)ever-changing risk landscape
To avoid falling prey to such scams, Morss, said, people can adopt the following simple precautions:
- Scrutinize e-mails and don’t open unfamiliar messages
- Do not fill out online forms from suspicious sources
- Check the validity of Web sites. Make inquiries to the head office or industry and government administrative bodies
- Be wary of attachments
- Do not give out credit card and other personal financial information online
Right now, the quantity of such spam, related to the Haiti disaster, is relatively low. However it’s current low-profile nature also makes it hard for security firms to identify and track the scam messages, said Morss.
Here’s a sample of one of the spam messages:
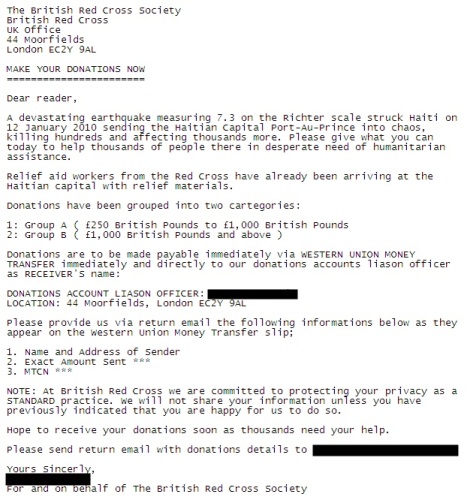
Scammers see humanitarian crises — such as the Haiti earthquake — as great opportunities to swindle people, according to Paul Wood, a Symantec employee.
“They count on the public’s good nature, concern, and desire to help and hope people won’t see through the scam e-mail they are reading,” Wood said in his blog on the Symantec site.
“The desire to help often clouds a person’s good judgment.”
Human curiosity is another effective element that works for spammers. For instance, in April last year, the Internet was flooded with spam messages purporting to contain information about celebrities who contracted the Swine flu.
The messages led unsuspecting surfers to phishing sites that either swiped their online personal data or sought to peddle them goods.
One Toronto-based security expert agrees.
“I’m quite familiar with this practice. Scammers hook onto issues about high profile personalities or attention grabbing headlines,” said Claudiu Popa, principal of Informatica Security Corp., a risk-management firm in Toronto.
Apart from 419 threats, Popa warned that networks of legitimate relief operations, run the risk of being hacked.
Many non-profit organizations hold extremely sensitive personal and financial data on their networks, which is very attractive to cybercriminals, he said.
“For hackers this is the enticing, low-hanging fruit.”
He said to protect the privacy and security of their clients’ online information, organizations and business should use the following tools:
- Firewalls to prevent intrusion and control network access
- Anti-virus software that detects malware and eliminates it
- Network scanners that automate network audits
- Intrusion detection systems
- Encryption tools to protect confidentiality of files and communications
- Authentication systems to validate and identify authorized system users
- Data destruction software to ensure sensitive information can not be recovered by criminal elements




