I have to hand it to cybercriminals, they’re wily and they’re hard working. They change tactics and techniques continuously to attract new prey and evade detection. Many are successful in tricking even the most suspicious-minded people.
This month Symantec has released information on a threat we’ve been monitoring for some time. Ransomware is a kind of malicious software that disables the computer in some way and sends a message demanding payment to restore functionality. It boils down to an extortion racket.
Ransomware has evolved to become very effective at separating victims from their money. As a result, Symantec believes instances of ransomware will soon surpass that of the ever-popular “fake AV” scam as the cybercrime strategy of choice. Symantec has discovered 16 different versions of the scam making the rounds so far. And that number is set to rise in the coming months, as new variations are quickly introduced in the social engineering behind the attacks.
In its early stages, ransomware would lock an infected computer’s screen and display a message promising to unlock the screen in return for payment. The strategy often displayed adult images on the screen of a locked computer to embarrass the victim into making a prompt payment.
New developments include techniques to trick the user into believing it to be action taken by law enforcement officials who have monitored untoward online activity. Also known as fake police ransomware, this malware pops up a message that may cite illegal downloads or browsing of adult websites as the reason the computer has been locked. To “avoid jail time” and regain access to your computer, the crooks’ message will insist users pay a fine immediately online. Some ransomware can enable a computer’s webcam and display the user’s face onscreen to make it seem as if they really are being watched! Perhaps it won’t be long before we see official-looking examples of ransomware accusing the victim of having illegally copied music or video files onto their computer.
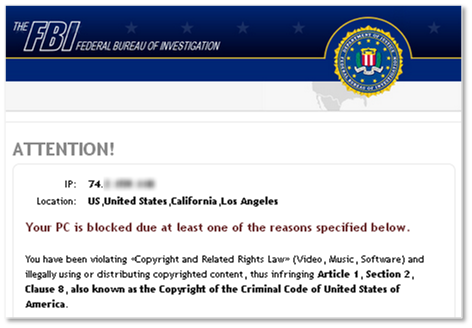
How does ransomware find its victims?
Ransomware is most commonly installed using two techniques: web exploits and drive-by downloads.
Drive-by download is when malware is installed on a user’s computer when that user browses a compromised website (in the case of fake police ransomware, the sites are typically pornographic in nature.) The download occurs in the background and is invisible to the user.
Do not pay the ransom!
What makes ransomware especially effective is that it preys upon a user’s fear of discovery. The message accuses users of engaging in illicit behaviour — an accusation that, right or wrong, may discourage users from seeking help or taking lengthy steps to unlock their computer. Paying a ransom may seem like the easiest way out – but don’t do it!
Symantec has found that even if the ransom is paid, the computer is unlikely to be restored. Crooks aren’t known for keeping promises. I can’t stress this enough – don’t pay the ransom!
How much is this scam worth?
The success rate of running a ransomware scam is about 3%, which may seem low – but volumes are high. With ransoms ranging from €50 to €100 in Europe, $100 in Canada and up to $200 USD in America, Symantec estimates a cybercriminal gang could make about $400,000 per month using this scam.

How to avoid the scam in the first place
Prevention is the best medicine. To avoid becoming a victim of a ransomware attack:
1. Ensure you have installed a good security software. Security software will warn you when you’ve wandered to a malicious website and will prevent malware from downloading to your computer.
2. Use the ‘think before you click’ method – never view, open, or execute any email attachment unless you expect it and trust the sender.
If you do find yourself a victim of ransomware, do not pay the ransom. Instead, follow the removal steps outlined here or check out this video for further instructions:
Other highlights from the Symantec Intelligence Report: October 2012
- Spam: 64.8 percent of total email globally (decrease of 10.2 percentage point since September 2012)
- Phishing: One in 286.9 emails identified as phishing globally (a decrease of 0.059 percentage points since September 2012)
- Malware: One in 229.4 emails contained malware (a decrease of 0.04 percentage points since September 2012)
By Paul Wood, Cyber Security Intelligence Manager, Symantec




