MessageLabs Intelligence recently tracked a new pharmaceutical spam campaign promoting a supposedly “Google-accredited” online pharmacy. This is obvious brand hijacking: Google does not host or approve any pharmacy sites.

We contacted Google about this, and a spokesperson responded with, “Google has a track record of fighting similar types of scams, and we also recommend that users carefully review online offers that look too good to be true before entering any of their information: http://googleblog.blogspot.com/2009/12/fighting-fraud-online-taking-google.html“.
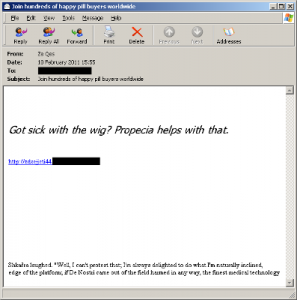
The spam message contains text promoting a drug for preventing hair loss, and a link to a blog the spammer has set up on a popular free blogging site, shown in the screenshot below:
[example of spam email promoting fake pharmacy brand]
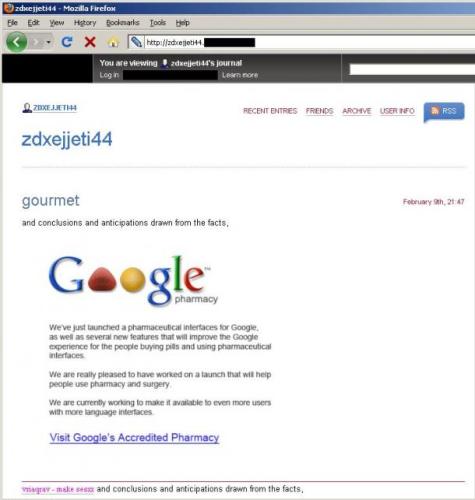
Anyone following the link will be directed to the spammer’s blog, containing spam-related content and links to the spammer’s actual site, as shown in the screenshot below:
[example of well-know free blog site being used to host brand-hijacking content]
In the last two days alone, we have automatically blocked over 250 similar spam-created blogs.
The blog’s most recent entry has a randomized, irrelevant title (“gourmet”), and consists of text taken from a book or some other document, interspersed with an image and link. The image contains the Google logo with the two “o” letters replaced by differently-shaped tablets. This is perhaps more plausible than it might seem due to Google’s famous “doodles”, where Google changes its logo to mark holidays or even famous computer scientists like the late Edsger W. Dijkstra.
The text below the logo (but still included in the image) incorrectly claims that Google has launched a “pharmaceutical interface”, followed by more text and finally underlined text in blue to appear like a link. It is likely that the spammer wants to capitalize on Google’s universally known name to add legitimacy to their products. With Google’s increasing diverse product range, spammers are perhaps hoping that a fake Google-accredited pharmacy will be plausible to some recipients.
The link (“vriagrav – make sesxx” [sic]) points to the spammer’s pharmaceutical site, an example of which can be seen below:
[example of the spam website relating to the spam campaign for the fake brand]
The image itself is not hosted on the blogging platform–instead it is hosted on a Russian site. The filename claims that the image is a GIF file, yet it is actually a JPEG file.
This type brand hijacking is a serious problem for well-known brands and can harm their reputation, as users might wrongly associate the nuisance factor of receiving such email with the brand.
(This blog was posted on behalf of Nick Johnston, Senior Software Engineer, Symantec.cloud)